eBay Covert Redirect Vulnerability Based on Googleads.g.doubleclick.net
(1) WebSite:
ebay.com
“eBay Inc. (stylized as ebay, formerly eBay) is an American multinational corporation and e-commerce company, providing consumer to consumer & business to consumer sales services via Internet. It is headquartered in San Jose, California. eBay was founded by Pierre Omidyar in 1995, and became a notable success story of the dot-com bubble. Today, it is a multi-billion dollar business with operations localized in over thirty countries.
The company manages eBay.com, an online auction and shopping website in which people and businesses buy and sell a broad variety of goods and services worldwide. In addition to its auction-style sales, the website has since expanded to include “Buy It Now" shopping; shopping by UPC, ISBN, or other kind of SKU (via Half.com); online classified advertisements (via Kijiji or eBay Classifieds); online event ticket trading (via StubHub); online money transfers (via PayPal) and other services." (Wikipedia)
(2) Vulnerability Description:
eBay web application has a computer cyber security problem. Hacker can exploit it by Covert Redirect attacks.
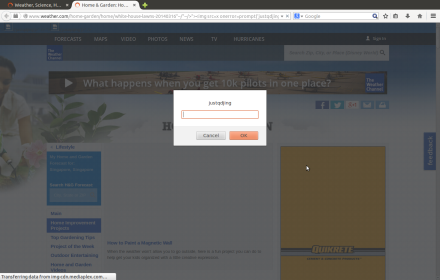
The vulnerability occurs at “ebay.com/rover” page with “&mpre” parameter, i.e.
The vulnerability can be attacked without user login. Tests were performed on Firefox (26.0) in Ubuntu (12.04) and IE (9.0.15) in Windows 7.
(2.1) When a user is redirected from eBay to another site, eBay will check whether the redirected URL belongs to domains in eBay’s whitelist, e.g.
google.com
If this is true, the redirection will be allowed.
However, if the URLs in a redirected domain have open URL redirection vulnerabilities themselves, a user could be redirected from eBay to a vulnerable URL in that domain first and later be redirected from this vulnerable site to a malicious site. This is as if being redirected from eBay directly.
One of the vulnerable domain is,
http://googleads.g.doubleclick.net (Google’s Ad system)
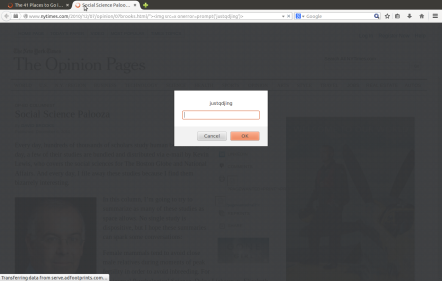
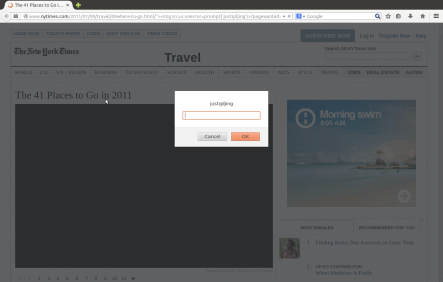
(2.2) Use one of webpages for the following tests. The webpage address is “http://itinfotech.tumblr.com/“. We can suppose that this webpage is malicious.
Vulnerable URL:
POC:
http://rover.ebay.com/rover/1/711-67261-24966-0/2?mtid=691&kwid=1&crlp=1_263602&itemid=370825182102&mpre=http://googleads.g.doubleclick.net/aclk?sa=L%26ai=C-RHnNvn2Uom8LeTaigfjkIHICfLQnccEAAAQASAAUNTx5Pf4_____wFgvwWCARdjYS1wdWItMDQ2NjU4MjEwOTU2NjUzMsgBBOACAKgDAaoEhQFP0LHofgVzg8U9Bvwu2_hN9Ow0n2tBH9xjKtngqcF6hgGQpxV6QzMgNxx0_UawPG3-UD097GLLCirbVMl2QxQqa04U3cp4YFgV5dshYbzmqlVVfNn-NuunzLNab6ATE5BUwQ9bgXBOW_qEz8qgbwVOvUJrn1IzL-ymANaKsQLZ9POlkbIe4AQBoAYV%26num=0%26sig=AOD64_3a3m_P_9GRVFc6UIGvnornMcLMoQ%26client=ca-pub-0466582109566532%26adurl=http://itinfotech.tumblr.com/
Poc Video:
https://www.youtube.com/watch?v=a4H-u17Y9ks
Blog Detail:
http://securityrelated.blogspot.com/2014/11/ebay-covert-redirect-vulnerability.html
(3) What is Covert Redirect?
Covert Redirect is a class of security bugs disclosed in May 2014. It is an application that takes a parameter and redirects a user to the parameter value without sufficient validation. This often makes use of Open Redirect and XSS vulnerabilities in third-party applications.
Covert Redirect is also related to single sign-on. It is known by its influence on OAuth and OpenID. Hacker may use it to steal users’ sensitive information. Almost all OAuth 2.0 and OpenID providers worldwide are affected. Covert Redirect was found and dubbed by a Mathematics PhD student Wang Jing from School of Physical and Mathematical Sciences, Nanyang Technological University, Singapore.
After Covert Redirect was published, it is kept in some common databases such as SCIP, OSVDB, Bugtraq, and X-Force. Its scipID is 13185, while OSVDB reference number is 106567. Bugtraq ID: 67196. X-Force reference number is 93031.
Discover and Reporter:
Wang Jing, Division of Mathematical Sciences (MAS), School of Physical and Mathematical Sciences (SPMS), Nanyang Technological University (NTU), Singapore. (@justqdjing)
http://tetraph.com/wangjing/
Related Articles:
http://tetraph.com/security/covert-redirect/ebay-covert-redirect-vulnerability
http://computerobsess.blogspot.com/2014/11/ebay-covert-redirect-vulnerability.html
https://webtechwire.wordpress.com/2014/06/05/ebay-bug/
https://twitter.com/tetraphibious/status/559167810543181825
http://aga.ustc.edu.cn/news/view?id=2094http://ittechnology.lofter.com/post/1cfbf60d_7063707
http://www.ustcif.com/default.php/content/2128/
http://itinfotech.tumblr.com/post/118850342491/covert-redirect
http://tetraph.blogspot.com/2014/11/ebay-covert-redirect-vulnerability.html
http://www.inzeed.com/kaleidoscope/covert-redirect/ebay-covert-redirect
https://itswift.wordpress.com/2014/06/02/ebay-bug/